ELECTROMAGNETIC PULSE (EMP) AND TEMPEST PROTECTION FOR FACILITIES
Table of Contents: http://jya.com/emp.htm
------------------------------------------------------------------------------
CHAPTER 8
EMP AND TEMPEST RISKS
8-1 Outline. This chapter is organized as follows:
8-1. Outline
8-2. Introduction
8-3. EMP environment--overview
a. General
(l) Classification of EMP
(2) High-altitude burst
(3) Generation of HEMP
(4) Compton electrons
(5) Relationships
b. Electric field
c. Magnetic field
d. Spatial extent
(1) Geographical coverage
(2) Surface area calculation
e. HEMP peak fields at the Earth's surface
(1) Orientation of Earth's geomagnetic field
(2) Geometric factors
8-4. Comparison of HEMP and lightning
8-5. TEMPEST risks
a. TEMPEST objectives
(1) Communication security (COMSEC)
(2) Parts of security
(3) Details of TEMPEST issues
(4) Theory of electromagnetic signal emanation
(5) Aim of TEMPEST discipline
b. Equipment emission characteristics
(1) RED and BLACK terminology
(2) Strength and nature of emanations
(3) Classes of equipment
(4) Project development brochure
c. Detection capabilities
(1) Electronic surveillance concerns
(2) Worst-case evaluation
d. TEMPEST isolation requirements
(1) Isolation approaches
(2) Recommended isolation concepts
(3) Design criteria
e. Installation within the shielded volume
(1) Precluding unintentional coupling
(2) Sources of additional information
(3) Limited exclusion area
(4) Spacing of equipment
(5) Penetrations
(6) Separating RED and BLACK
(7) Telephones and intercoms
f. Related TEMPEST documents
(1) National Security Agency documents
(2) National COMSEC Information Memorandums
8-6. Cited references
------------------------------------------------------------------------------
8-2. Introduction. System design greatly influences the impact a HEMP event
has on a facility. Thorough knowledge of the various modes of HEMP coupling
to structures combined with system sensitivity information and TEMPEST risks
can give designers better insight into HEMP hardening and TEMPEST protection
requirements for critical facilities.
8-3. EMP environment--overview.
a. General.
(1) Classification of EMP. EMP can exist in many forms. Typically,
EMP is classified in terms of the height of burst (HOB) of the detonation and
its relative relationship with respect to the target or observer. For this
pamphlet, only the high-altitude detonation is considered since this
environment can be considered for all critical facilities. Additional
scenario-dependent environments would apply to targeted facilities or those
located near targets.
(2) High-altitude burst. A high-altitude burst occurs above
approximately 30 kilometers and differs from surface and air bursts in that
other associated nuclear effects do not occur on the ground. EMP is the major
effect.
(3) Generation of HEMP. Figure 8-1 depicts the generation of HEMP.
The gamma rays produced by the burst travel radially from the burst in a
spherical shell that expands at the speed of light. Below 30 kilometers, the
atmosphere is dense enough to cause gamma rays to be absorbed by Compton
scattering. This effect results when gamma rays from the nuclear burst
collide with air molecules. Absorption is nearly complete by the time the
gamma rays reach an altitude of 20 kilometers. Thus, the source region for a
high-altitude burst is located between 20 and 30 kilometers above the Earth's
surface. This region is shaped like a pancake and its lateral extent is
limited only by the curvature of the Earth.
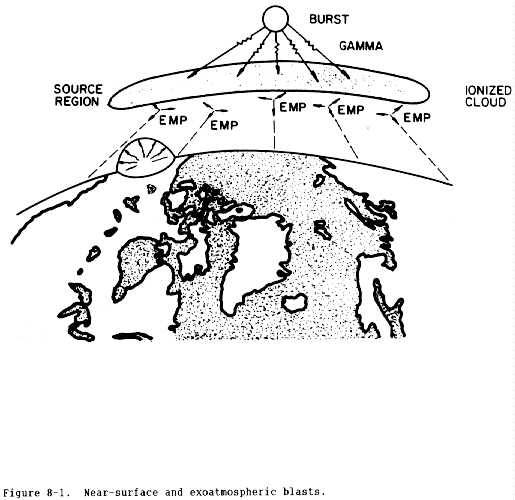 (4) Compton electrons. At the altitude of the source region, the
Compton electrons travel about 100 meters before they are absorbed. While
traveling this distance, the electrons are strongly deflected by the Earth's
geomagnetic field, making them turn with a radius of about 100 meters. Thus,
the Compton current has large components in nonradial directions from the
burst, i.e., transverse to the direction of the gamma-ray propagation, which
are effective in generating radiated fields. The transverse Compton current
is the primary source of high-altitude radiated EMP. HEMP consists of
radiated electric and magnetic fields that begin almost at once and persist
for more than 100 seconds. Typically, for design-related considerations, only
the fields produced in the first microsecond (early time) after the burst are
considered. However, as the impacts of intermediate and late-time effects
become better defined, additional consideration may be required.
(5) Relationships. In general, characteristics such as the spatial
extent, time waveform, and peak amplitude of HEMP depend on the HOB, weapon
yield, and observer's location with respect to the burst. The following
paragraphs show the characteristics of a nonclassified but representative
HEMP.
b. Electric field. The time waveform of a HEMP electric field, E(t), in
free space can be approximated by the analytic
expression--
kEpkea(t-ts)
E(t) = --------------(kV/m)
l+e(a+b)(t-ts)
(eq 8-1)
where the coefficients are given by--
Epk = 50 kVtm, the peak electric field (kV/meter)
k = 1.2, a normalization constant
a = 5 x 108 sec-1, the exponential rise rate (sec-1)
b = 2.3 x 107 sec-1, the exponential decay rate (sec-1)
Ts = 10-8 sec, the time shift parameter (sec)
t = the time of interest (sec).
Figure 8-2 is a graphic representation of the HEMP waveform.
(4) Compton electrons. At the altitude of the source region, the
Compton electrons travel about 100 meters before they are absorbed. While
traveling this distance, the electrons are strongly deflected by the Earth's
geomagnetic field, making them turn with a radius of about 100 meters. Thus,
the Compton current has large components in nonradial directions from the
burst, i.e., transverse to the direction of the gamma-ray propagation, which
are effective in generating radiated fields. The transverse Compton current
is the primary source of high-altitude radiated EMP. HEMP consists of
radiated electric and magnetic fields that begin almost at once and persist
for more than 100 seconds. Typically, for design-related considerations, only
the fields produced in the first microsecond (early time) after the burst are
considered. However, as the impacts of intermediate and late-time effects
become better defined, additional consideration may be required.
(5) Relationships. In general, characteristics such as the spatial
extent, time waveform, and peak amplitude of HEMP depend on the HOB, weapon
yield, and observer's location with respect to the burst. The following
paragraphs show the characteristics of a nonclassified but representative
HEMP.
b. Electric field. The time waveform of a HEMP electric field, E(t), in
free space can be approximated by the analytic
expression--
kEpkea(t-ts)
E(t) = --------------(kV/m)
l+e(a+b)(t-ts)
(eq 8-1)
where the coefficients are given by--
Epk = 50 kVtm, the peak electric field (kV/meter)
k = 1.2, a normalization constant
a = 5 x 108 sec-1, the exponential rise rate (sec-1)
b = 2.3 x 107 sec-1, the exponential decay rate (sec-1)
Ts = 10-8 sec, the time shift parameter (sec)
t = the time of interest (sec).
Figure 8-2 is a graphic representation of the HEMP waveform.
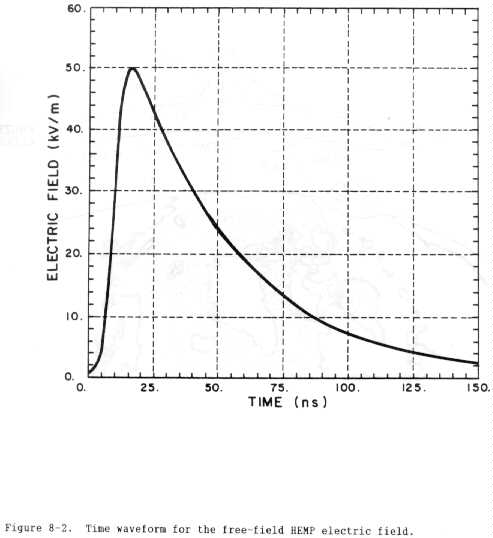 c. Magnetic field. The associated magnetic component of the radiated HEMP
field can be obtained by dividing the electric field in volts per meter by 377
ohms. This gives the magnetic field in amps per meter with a peak value of
about 135 amps per meter. It should be noted, however, that the values shown
in figure 8-2 apply only to the free-field environment and not to the behavior
of fields near conducting surfaces such as the surface of the Earth. Near
such a conductor, the electric field will be much smaller because it is
shorted out, whereas the magnetic field will be about twice its value in free
space, or almost 270 amps per meter.
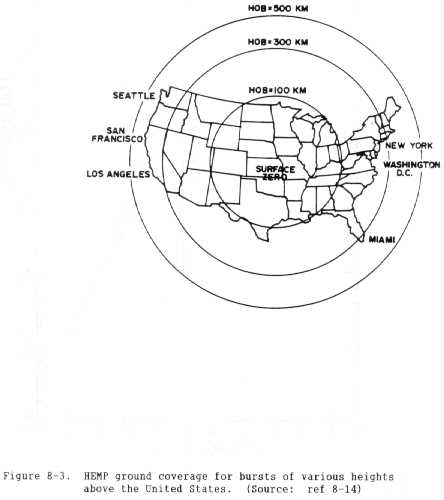
d. Spatial extent.
(1) Geographical coverage. The geographical coverage of HEMP over the
Earth's surface is determined entirely by the HOB. The maximum ground range
(tangent radius) depends on the tangent to the Earth from the burst point and
is the arc length between this tangent and the point on the Earth's surface
directly beneath the burst surface zero. To approximate this distance, the
following calculation for tangent radius RT (in kilometers) can be made:
RE
RT = RE cos-1(----------)
RE + HOB
(eq 8-2)
where RE = 6370 kilometers (the approximate radius of the Earth) and HOB is
the burst height in kilometers.
(2) Surface area calculation. The total surface area AT in square
kilometers covered by HEMP can be calculated as follows:
2(pi)RE2 HOB
AT = ------------
RE + HOB
(eq 8-3)
Figure 8-3 applies this information to the United States, showing ground
coverage for bursts of 50 and 120 miles over the central portion.
c. Magnetic field. The associated magnetic component of the radiated HEMP
field can be obtained by dividing the electric field in volts per meter by 377
ohms. This gives the magnetic field in amps per meter with a peak value of
about 135 amps per meter. It should be noted, however, that the values shown
in figure 8-2 apply only to the free-field environment and not to the behavior
of fields near conducting surfaces such as the surface of the Earth. Near
such a conductor, the electric field will be much smaller because it is
shorted out, whereas the magnetic field will be about twice its value in free
space, or almost 270 amps per meter.
d. Spatial extent.
(1) Geographical coverage. The geographical coverage of HEMP over the
Earth's surface is determined entirely by the HOB. The maximum ground range
(tangent radius) depends on the tangent to the Earth from the burst point and
is the arc length between this tangent and the point on the Earth's surface
directly beneath the burst surface zero. To approximate this distance, the
following calculation for tangent radius RT (in kilometers) can be made:
RE
RT = RE cos-1(----------)
RE + HOB
(eq 8-2)
where RE = 6370 kilometers (the approximate radius of the Earth) and HOB is
the burst height in kilometers.
(2) Surface area calculation. The total surface area AT in square
kilometers covered by HEMP can be calculated as follows:
2(pi)RE2 HOB
AT = ------------
RE + HOB
(eq 8-3)
Figure 8-3 applies this information to the United States, showing ground
coverage for bursts of 50 and 120 miles over the central portion.
 e. HEMP peak fields at the Earth's surface.
(1) Orientation of Earth's geomagnetic field. Since the motion of the
compton electrons depends on the orientation of the Earth's geomagnetic field,
the incident HEMP fields vary significantly in peak amplitude, rise time, and
duration over the large area affected by the HEMP. The maximum peak electric
field Emax occurs just south of ground zero and can be as high as 50 kilovolts
per meter, depending on the HOB and the weapon yield. The peak field Epk
observed at any other location is some fraction of Emax.
(2) Geometric factors. In addition to the orientation and dip of the
geomagnetic field, geometric factors based on the observer's position with
respect to the burst also cause spatial variations of the HEMP field strength.
In the figure, the null area slightly north of the burst point is produced by
the geomagnetic dip over the CONUS; Compton electrons created in the same
direction as the Earth's geomagnetic field do not turn and no radiated fields
are created. The maximum peak fields are found at a distance equal to about
twice the HOB south of surface zero.
8-4. Comparison of HEMP and lightning. HEMP-induced surge currents on
overhead transmission lines are similar to, but not exactly the same as,
lightning-induced surges. Table 8-1 compares worst-case surges. From the
numerical values, it could be inferred that lightning is a more serious
threat. The values for lightning, however, represent the 99th percentile of
all measurements on standard lightning discharges, and thus may not be
representative of the strokes that occur near a given facility. In contrast,
the HEMP pulse is not a localized phenomenon, but illuminates a very wide
area. As a result, any hardened facility would see a HEMP-induced current if
there were a war, while it might never be exposed to the maximum lightning
current. In addition, there are significant differences in pulse rate and
frequency content. For this reason, it cannot be assumed that standard
lightning protection is an adequate substitute for HEMP protection.
8-5. TEMPEST risks.
a. TEMPEST objectives.
(1) Communication security (COMSEC). Communication security (COMSEC)
is the term used to denote steps taken to prevent disclosure of national
security information to unauthorized recipients during the communication
process. NTISSI 7000 and AR 530-4 define minimum measures that must be taken
to protect CONUS facilities (refs 8-1 and 8-2). The information to be guarded
includes plain text of classified messages, as well as cryptographic
technology and materials. Cryptographic information is especially sensitive,
not as an end in itself, but because it is used to protect other classified
data. If the integrity of an encryption system is breached at any point, all
classified information protected by that coding may be compromised.
(2) Parts of COMSEC. COMSEC consists of four main parts: physical
security--all physical measures to safeguard materials from unauthorized
access; emissions security-control of emanations from equipments processing
classified data; transmission security--protection of transmissions from
traffic analysis, imitative deception, and disruption; and cryptographic
security--the use of technically sound cryptosystems. Only the emissions
security discipline or TEMPEST is specifically addressed in this manual.
(3) Details of TEMPEST issues. Because the details of many TEMPEST
issues are classified and controlled under strict conditions of need-to-know,
the following discussions must be somewhat general. Nevertheless, it provides
the reader with a needed aPpreciation of TEMPEST fundamentals.
(4) Theory of electromagnetic signal emanation. Any
electrical/electronic circuit that carries a time-varying current will emanate
electromagnetic signals with the strength of the emission proportional to the
current amplitude and its time rate of change. These signals propagate
outward from the source as free space waves and as guided waves along
conductors connected to or close to the radiator. If time variations of the
source currents are related in any way to the information content of the
signals (which will almost certainly be the case on a data line~, then the
emanation will also bear some relationship to the data. It may, therefore, be
possible to reconstruct the original intelligence by analysis of these
unintentional emissions.
(5) Aim of TEMPEST discipline. Finally, if the source information is
classified, interception and analysis of the emanations by unauthorized
personnel will compromise national security. The aim of the TEMPEST
discipline is to control stray emissions in a manner that prevents such
disclosures.
b. Equipment emission characteristics.
(1) RED and BLACK terminology. Before addressing the emission
characteristics issue, the RED and BLACK terminology will first be introduced.
A RED equipment or circuit is one that handles plain text information with
national security value. Equipment processing signals that are unclassified,
either because of content of the text or because the intelligence is obscured
by encryption, is denoted in BLACK.
(2) Strength and nature of emanations. The unintentional emission
characteristics of RED systems and equipments are categorized according to
strength and nature of their emanations. The reason for the strength element
is clear: high-level signals can be intercepted at magnitudes that permit
analysis with greater physical separations between the source and the
eavesdropper. The second factor relates to the correlation between waveform
of the emitted signal and the information to be protected.
(3) Classes of equipment. For purposes of facility engineering and
construction within the limitations of this manual, it is only necessary to
define two classes:
(a) Equipments that are TEMPEST-approved according to the criteria
established in the current edition of NACSIM 5100 (ref 8-3).
(b) All equipments that have not been TEMPEST-tested or are
nonapproved.
(4) Project development brochure. Information regarding the category
of RED equipment to be protected should be presented in the project
development brochure prepared by the user of the facility.
c. Detection capabilities.
(1) Electromagnetic surveillance concerns. Concerns about
electromagnetic surveillance have been intensified by advances in state-of-
the-art equipment design and signal processing techniques. While a few
technologies such as fiber optics and multiplexing have made interception and
analysis more difficult, the overall effect has been to open new opportunities
for eavesdroppers. Projections into the immediate future indicate that this
trend will continue.
(2) Worst-case evaluation. The only safe approach is a reasonable
worst-case evaluation. It must be assumed that the opposition has the proper
equipment to monitor all signals of significant amplitude in areas where
access is uncontrolled.
d. TEMPEST isolation requirements.
(1) Isolation approaches. Encryption is the method used to guard
against disclosure of classified information when long-distance
telecommunications are monitored. However, it does not prevent possible
compromise through interceptions and analyses of unintentional emanations from
RED equipments.
(a) Many approaches are available to equipment and facility
designers to avoid disclosures through potentially compromising emanations.
All of these techniques reduce the stray signal strength at locations where
access is uncontrolled, so that the intelligence content is lost in the
background electrical noise. AR 530-4 should be consulted to determine the
level of protection required.
(b) Examples of preventive measures include the following:
- Physical separation--excluding unauthorized individuals from
areas near the source where the emanations are larger in amplitude than the
ambient noise.
- Electromagnetic separation--the use of shielding, filtering,
and other methods of EM isolation to attenuate the unintentional emissions.
- Signal level minimization--design and operation of circuits at
lowest feasible power levels to minimize the strength of unintentional
emissions.
(c) These methods can be employed in an infinite variety of
combinations to achieve the desired goals.
(2) Recommended TEMPEST isolation concept. NTISSI 7000 and AR 530-4
analysis is the first step in determining needed TEMPEST countermeasures.
Shielding for TEMPEST is not necessarily required; however, for facilities
having high-confidence HEMP survivability specifications and being hardened in
accordance with recommendations of this manual, it is technically prudent and
highly cost-effective to include TEMPEST shielding and penetration protection
in a common subsystem. The suggested TEMPEST isolation concept takes
advantage of this principle.
(a) The first requirement, a physical security measure, is the
establishment of a controlled space (CS) containing the equipment to be
TEMPEST-protected and within which access is not available to those not
authorized to receive the information being processed at the site.
(b) NACSEM 5204 defines the detailed procedures to compute shielding
effectiveness requirements for specific TEMPEST applications (ref 8-4).
Parameters of the problem include measured emission characteristics of the
equipments and distance to the perimeter of the controlled space. The
calculation determines the attenuation needed to reduce emanation levels below
detectable limits in the ambient noise environment. If reasonable worst-case
assumptions are made regarding the variables, however, then 50 decibels
(nominal) attenuation is adequate for an installation within CONUS. This
requirement can be met by a shield and penetration treatments that conform to
Specification NSA No. 73-2A.
(c) NSA 73-2A is an appendix in NACSEM 5204. The document also
contains Specifications NSA No. 65-5 and 65-6 for TEMPEST applications where
greater shielding effectiveness requirements exist. DIAM 50-3A should be
consulted for SCIF shielding information (ref 8-5).
(3) TEMPEST design criteria. Since electromagnetic performance
requirements of a 50-decibel (nominal) TEMPEST design are quite consistent
with performance necessary for HEMP considerations and only a few additional
features are prescribed for the shielding and penetration protection
subsystem, the reasonable worst-case TEMPEST assumptions have been
incorporated into the recommended HEMP/TEMPEST approach. The following
paragraphs summarize the TEMPEST-unique requirements for facility design.
(a) Shielding effectiveness. Minimum attenuation levels of the
shielded enclosure, when measured in accordance with NSA 73-2A, are as shown
in figure 8-4. This curve contains a slight increase in the requirements at
frequencies above 500 megahertz compared with values prescribed in NSA 73-2A.
The upper frequency of the shielding effectiveness and filter insertion loss
frequency have also been extended as high as 10 gigahertz. The site-specific
requirements should be determined by consulting with the using agency.
e. HEMP peak fields at the Earth's surface.
(1) Orientation of Earth's geomagnetic field. Since the motion of the
compton electrons depends on the orientation of the Earth's geomagnetic field,
the incident HEMP fields vary significantly in peak amplitude, rise time, and
duration over the large area affected by the HEMP. The maximum peak electric
field Emax occurs just south of ground zero and can be as high as 50 kilovolts
per meter, depending on the HOB and the weapon yield. The peak field Epk
observed at any other location is some fraction of Emax.
(2) Geometric factors. In addition to the orientation and dip of the
geomagnetic field, geometric factors based on the observer's position with
respect to the burst also cause spatial variations of the HEMP field strength.
In the figure, the null area slightly north of the burst point is produced by
the geomagnetic dip over the CONUS; Compton electrons created in the same
direction as the Earth's geomagnetic field do not turn and no radiated fields
are created. The maximum peak fields are found at a distance equal to about
twice the HOB south of surface zero.
8-4. Comparison of HEMP and lightning. HEMP-induced surge currents on
overhead transmission lines are similar to, but not exactly the same as,
lightning-induced surges. Table 8-1 compares worst-case surges. From the
numerical values, it could be inferred that lightning is a more serious
threat. The values for lightning, however, represent the 99th percentile of
all measurements on standard lightning discharges, and thus may not be
representative of the strokes that occur near a given facility. In contrast,
the HEMP pulse is not a localized phenomenon, but illuminates a very wide
area. As a result, any hardened facility would see a HEMP-induced current if
there were a war, while it might never be exposed to the maximum lightning
current. In addition, there are significant differences in pulse rate and
frequency content. For this reason, it cannot be assumed that standard
lightning protection is an adequate substitute for HEMP protection.
8-5. TEMPEST risks.
a. TEMPEST objectives.
(1) Communication security (COMSEC). Communication security (COMSEC)
is the term used to denote steps taken to prevent disclosure of national
security information to unauthorized recipients during the communication
process. NTISSI 7000 and AR 530-4 define minimum measures that must be taken
to protect CONUS facilities (refs 8-1 and 8-2). The information to be guarded
includes plain text of classified messages, as well as cryptographic
technology and materials. Cryptographic information is especially sensitive,
not as an end in itself, but because it is used to protect other classified
data. If the integrity of an encryption system is breached at any point, all
classified information protected by that coding may be compromised.
(2) Parts of COMSEC. COMSEC consists of four main parts: physical
security--all physical measures to safeguard materials from unauthorized
access; emissions security-control of emanations from equipments processing
classified data; transmission security--protection of transmissions from
traffic analysis, imitative deception, and disruption; and cryptographic
security--the use of technically sound cryptosystems. Only the emissions
security discipline or TEMPEST is specifically addressed in this manual.
(3) Details of TEMPEST issues. Because the details of many TEMPEST
issues are classified and controlled under strict conditions of need-to-know,
the following discussions must be somewhat general. Nevertheless, it provides
the reader with a needed aPpreciation of TEMPEST fundamentals.
(4) Theory of electromagnetic signal emanation. Any
electrical/electronic circuit that carries a time-varying current will emanate
electromagnetic signals with the strength of the emission proportional to the
current amplitude and its time rate of change. These signals propagate
outward from the source as free space waves and as guided waves along
conductors connected to or close to the radiator. If time variations of the
source currents are related in any way to the information content of the
signals (which will almost certainly be the case on a data line~, then the
emanation will also bear some relationship to the data. It may, therefore, be
possible to reconstruct the original intelligence by analysis of these
unintentional emissions.
(5) Aim of TEMPEST discipline. Finally, if the source information is
classified, interception and analysis of the emanations by unauthorized
personnel will compromise national security. The aim of the TEMPEST
discipline is to control stray emissions in a manner that prevents such
disclosures.
b. Equipment emission characteristics.
(1) RED and BLACK terminology. Before addressing the emission
characteristics issue, the RED and BLACK terminology will first be introduced.
A RED equipment or circuit is one that handles plain text information with
national security value. Equipment processing signals that are unclassified,
either because of content of the text or because the intelligence is obscured
by encryption, is denoted in BLACK.
(2) Strength and nature of emanations. The unintentional emission
characteristics of RED systems and equipments are categorized according to
strength and nature of their emanations. The reason for the strength element
is clear: high-level signals can be intercepted at magnitudes that permit
analysis with greater physical separations between the source and the
eavesdropper. The second factor relates to the correlation between waveform
of the emitted signal and the information to be protected.
(3) Classes of equipment. For purposes of facility engineering and
construction within the limitations of this manual, it is only necessary to
define two classes:
(a) Equipments that are TEMPEST-approved according to the criteria
established in the current edition of NACSIM 5100 (ref 8-3).
(b) All equipments that have not been TEMPEST-tested or are
nonapproved.
(4) Project development brochure. Information regarding the category
of RED equipment to be protected should be presented in the project
development brochure prepared by the user of the facility.
c. Detection capabilities.
(1) Electromagnetic surveillance concerns. Concerns about
electromagnetic surveillance have been intensified by advances in state-of-
the-art equipment design and signal processing techniques. While a few
technologies such as fiber optics and multiplexing have made interception and
analysis more difficult, the overall effect has been to open new opportunities
for eavesdroppers. Projections into the immediate future indicate that this
trend will continue.
(2) Worst-case evaluation. The only safe approach is a reasonable
worst-case evaluation. It must be assumed that the opposition has the proper
equipment to monitor all signals of significant amplitude in areas where
access is uncontrolled.
d. TEMPEST isolation requirements.
(1) Isolation approaches. Encryption is the method used to guard
against disclosure of classified information when long-distance
telecommunications are monitored. However, it does not prevent possible
compromise through interceptions and analyses of unintentional emanations from
RED equipments.
(a) Many approaches are available to equipment and facility
designers to avoid disclosures through potentially compromising emanations.
All of these techniques reduce the stray signal strength at locations where
access is uncontrolled, so that the intelligence content is lost in the
background electrical noise. AR 530-4 should be consulted to determine the
level of protection required.
(b) Examples of preventive measures include the following:
- Physical separation--excluding unauthorized individuals from
areas near the source where the emanations are larger in amplitude than the
ambient noise.
- Electromagnetic separation--the use of shielding, filtering,
and other methods of EM isolation to attenuate the unintentional emissions.
- Signal level minimization--design and operation of circuits at
lowest feasible power levels to minimize the strength of unintentional
emissions.
(c) These methods can be employed in an infinite variety of
combinations to achieve the desired goals.
(2) Recommended TEMPEST isolation concept. NTISSI 7000 and AR 530-4
analysis is the first step in determining needed TEMPEST countermeasures.
Shielding for TEMPEST is not necessarily required; however, for facilities
having high-confidence HEMP survivability specifications and being hardened in
accordance with recommendations of this manual, it is technically prudent and
highly cost-effective to include TEMPEST shielding and penetration protection
in a common subsystem. The suggested TEMPEST isolation concept takes
advantage of this principle.
(a) The first requirement, a physical security measure, is the
establishment of a controlled space (CS) containing the equipment to be
TEMPEST-protected and within which access is not available to those not
authorized to receive the information being processed at the site.
(b) NACSEM 5204 defines the detailed procedures to compute shielding
effectiveness requirements for specific TEMPEST applications (ref 8-4).
Parameters of the problem include measured emission characteristics of the
equipments and distance to the perimeter of the controlled space. The
calculation determines the attenuation needed to reduce emanation levels below
detectable limits in the ambient noise environment. If reasonable worst-case
assumptions are made regarding the variables, however, then 50 decibels
(nominal) attenuation is adequate for an installation within CONUS. This
requirement can be met by a shield and penetration treatments that conform to
Specification NSA No. 73-2A.
(c) NSA 73-2A is an appendix in NACSEM 5204. The document also
contains Specifications NSA No. 65-5 and 65-6 for TEMPEST applications where
greater shielding effectiveness requirements exist. DIAM 50-3A should be
consulted for SCIF shielding information (ref 8-5).
(3) TEMPEST design criteria. Since electromagnetic performance
requirements of a 50-decibel (nominal) TEMPEST design are quite consistent
with performance necessary for HEMP considerations and only a few additional
features are prescribed for the shielding and penetration protection
subsystem, the reasonable worst-case TEMPEST assumptions have been
incorporated into the recommended HEMP/TEMPEST approach. The following
paragraphs summarize the TEMPEST-unique requirements for facility design.
(a) Shielding effectiveness. Minimum attenuation levels of the
shielded enclosure, when measured in accordance with NSA 73-2A, are as shown
in figure 8-4. This curve contains a slight increase in the requirements at
frequencies above 500 megahertz compared with values prescribed in NSA 73-2A.
The upper frequency of the shielding effectiveness and filter insertion loss
frequency have also been extended as high as 10 gigahertz. The site-specific
requirements should be determined by consulting with the using agency.
 (b) Shield doors. TEMPEST shield design includes a shielded
vestibule entrance arrangement with two doors oriented at 90 degrees to each
other. The purpose of double doors is the same as that cited for HEMP--to
preserve the shielding effectiveness during actual entries and exits.
Effectiveness requirements for the doors are the same as those for the main
shield.
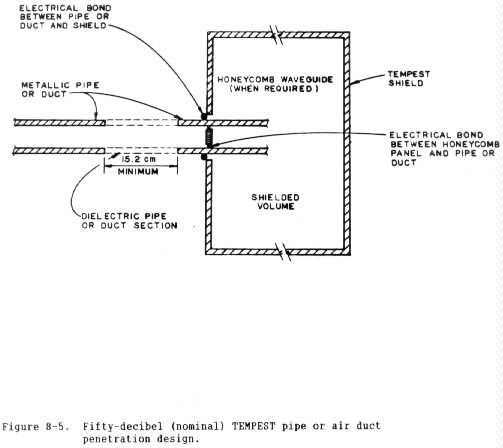
(c) Piping and ventilation penetration. Mechanical penetrations,
piping, and air ducts are to be bonded to the shield at the point of
penetration. The design must be configured as a waveguide-beyond-cutoff to
attenuate all frequencies within the specified band, as shown in figure 8-5.
(b) Shield doors. TEMPEST shield design includes a shielded
vestibule entrance arrangement with two doors oriented at 90 degrees to each
other. The purpose of double doors is the same as that cited for HEMP--to
preserve the shielding effectiveness during actual entries and exits.
Effectiveness requirements for the doors are the same as those for the main
shield.
(c) Piping and ventilation penetration. Mechanical penetrations,
piping, and air ducts are to be bonded to the shield at the point of
penetration. The design must be configured as a waveguide-beyond-cutoff to
attenuate all frequencies within the specified band, as shown in figure 8-5.
 (d) Electrical penetration. The specification requires that a
filter providing at least 50 decibels of insertion loss from 14 kilohertz to
the upper design protection frequency, typically 1 to 10-gigahertz upper
frequency when measured in accordance with procedures of MIL-STD-220A, be
installed on each power, telephone, and signal line that penetrates the
enclosure shield wall (ref 8-6). (Note: Other forms of isolation, such as
optical or pneumatic decouplers, which accomplish the same purpose, may be
used and special performance specifications for filters on conductors with
operating signals in the 14 kilohertz to 1-10 gigahertz band may be
established, subject to the approval of the using agency.)
e. Installation within the shielded volume.
(1) Precluding unintentional coupling. It is virtually certain that
the volume enclosed by the TEMPEST shield will contain some BLACK equipment
and wiring, as well as RED circuits that handle national security information.
Therefore, the facility design and hardware/wiring layouts must preclude
unintentional coupling of RED emanations into BLACK conductors. These
measures are above and beyond the shielding and penetration protection
subsystem features and are necessary whether or not a shield is provided.
(2) Sources of additional information. The guidelines and requirements
for RED/BLACK isolation are published in NACSIM 5203 (ref 8-7) and MIL-HDBK-
232A (ref 8-8). Since some details of the specified practices are classified,
this discussion must be considered incomplete, and the designer must also
consult NACSIM 5203 and MIL-HDBK-232A to comply with the minimum requirements.
(3) Limited exclusion area. The room or area within which RED
equipment is located and to which controls are applied for protection of
national security information is known as a limited exclusion area (LEA). The
TEMPEST shield may enclose part or all of the LEA and might also envelope
other sPaces.
(4) Spacing of equipment. RED equipment must be physically separated
from the facility walls and ceiling, from BLACK equipment and wiring, and from
utility conductors such as ventilation ducts and piping. Minimum required
spacings depend on whether the RED equipment is low-level signaling, TEMPEST-
approved hardware or not, and on the nature of possible propagation paths
between the BLACK element and an area of uncontrolled access.
(5) Penetrations. Physical separation practices, as well as special
shielding and distribution (for example, using conduits, ducts, and trays)
instructions, also apply between RED and BLACK wiring in the LEA. Specific
guidelines are presented in NACSIM 5203 for signal lines,
telephone/communication cables, power feeders, ground wires and other utility
(air-conditioning control and status, fire alarm) electrical conductors.
Markings with paint or tape are prescribed to distinguish RED wiring runs from
BLACK cables, and RED conduits must be accessible for inspection.
(6) Separating RED and BLACK. Also, depending on characteristics of
the RED equipment, separate filter-isolated RED and BLACK power distribution
subsystems or individual equipment power filters may be required. Further, it
may be necessary to provide separate and distinctively identified RED and
BLACK convenience outlets.
(7) Telephones and intercoms. Administrative telephone and facility
intercommunication subsystems require particular attention. The most
effective protection is to eliminate or, at least, minimize the number of
instruments in the LEA. If exclusion is not practical, separation, shielding,
and filter isolation devices and positive disconnect capabilities are to be
provided as prescribed in NACSIM 5203.
f. Related TEMPEST documents.
(1) National Security Agency documents. The reader desiring additional
background material concerning TEMPEST and needing specific implementation
information is directed to the series of TEMPEST source documents published by
the National Security Agency (NSA). Supplementary use of these references
during facility design and construction phases is imperative because
classification considerations limit the information incorporated in this
manual to generalized discussions. Only the shielding and penetration
protection requirements are included in this manual.
(2) National COMSEC Information Memorandums. NACSIM 5000 provides an
overall introduction to the TEMPEST discipline (ref 8-9). NACSIM 5203 and
NACSEM 5204 are essential to the project for defining installation
requirements within the protected volume and the shielded enclosure
requirements, respectively (refs 8-7 and 8-4). Other documents to which the
reader may wish to refer include: NACSI 5004 (ref 8-1), NACSI 5005 (ref 8-
10), NACSIM 5100A (ref 8-3), NACSEM 5109 (ref 8-11), NACSEM 5110 (ref 8-12),
and NACSEM 5201 (ref 8-13). The military departments (MILDEPs) also publish
TEMPEST regulations and guidance; access to these documents can be obtained
through the appropriate MILDEP communication security agency.
8-6. Cited references.
8-1. National Telecommunications and Information System Security
Instruction (NTISSI) 7000, 17 October 1988.
8-2. Army Regulation (AR) 530-4, (U) Control of Compromising Emanations
(Headquarters, Department of the Army [HQDA]) (C).
8-3. National COMSEC Information Memorandum (NACSIM) 5100A, (U)
Compromising Emanations Laboratory Test Requirements,
Electromagnetics (NSA) (C).
8-4. National COMSEC/Emergency Security (EMSEC) Information Memorandum
(NACSEM) 5204, (U) Shielded Enclosures (NSA, January 1979) (C).
8-5. Defense Intelligence Agency Memorandum (DIAM) 50-3A, Physical
Security Standards for Sensitive Compartmented Information
Facilities (Defense Intelligence Agency, 2 October 1984).
8-6. Military Standard (MIL-STD) 220A, Method of Insertion-Loss
Measurement (Department of Defense [DOD], 15 December 1959).
8-7. NACSIM 5203, (U) Guidelines for Facility Design and RED/BLACK
Installation (NSA, 30 June 1982) (C).
8-8. Military Handbook (MIL-HDBK) 232A, (U) RED/BLACK Engineering
Guidelines (DOD, 25 April 1980) (C).
8-9. NACSIM 5000, (U) TEMPEST Fundamentals (NSA, 1 February 1982) (C).
8-10. National COMSEC Instruction (NACSI) 5005, (U) TEMPEST
Countermeasures for Facilities Outside the United States (NSA,
January 1984) (S).
8-11. NACSEM 5109, (U) TEMPEST Testing Fundamentals (NSA) (C).
8-12. NACSEM 5110, (U) Facility Evaluation Criteria--TEMPEST (NSA, July
1973) (S).
8-13. NACSEM 5201, (U) TEMPEST Guidelines for Equipment/System Design
(NSA, September 1978) (C).
8-14. DNA EMP Course Study Guide, draft prepared for Defense Nuclear
Agency (The BDM Corporation, April 1983).
Table 8-1. Comparison of HEMP with lightning-induced stresses
on long overhead power lines.
_________________________________________________________________________________
HEMP Vmax Imax dV/dt dI/dt S/Idt2 S/I dt S/IVdt
phenomenon (MV) (kA) (kV/ns) (A/ns) (Coulombs) (A2-sec) (Joules)
_________________________________________________________________________________
HEMP on long 6 14 40 100 10-2 150 6x104
overhead power
lines
_________________________________________________________________________________
HEMP on short 1 2.5 40 100 2x10-3 5 2x103
overhead power
lines
_________________________________________________________________________________
HEMP on buried 1 2.5 8 20 -- -- --
power lines
_________________________________________________________________________________
Direct lightning
strokes (Max) 100 100 0.8 to 8 2 to 100 40 3.1xl06 1.2x108
(Typical) 10 25
_________________________________________________________________________________
Indirect light-
ning strokes
(Max) 6 15 -- -- 4.5 1.8x104 7x106
_________________________________________________________________________________
Voltage computations assume a nominal power line surge impedance of 400 ohms.
Lightning discharge estimates do not consider so-called "positive superbolts"
which are anomalies, but are roughly l0 times more severe than normal
lightning bolts.
_________________________________________________________________________________
[End Chapter 8]
(d) Electrical penetration. The specification requires that a
filter providing at least 50 decibels of insertion loss from 14 kilohertz to
the upper design protection frequency, typically 1 to 10-gigahertz upper
frequency when measured in accordance with procedures of MIL-STD-220A, be
installed on each power, telephone, and signal line that penetrates the
enclosure shield wall (ref 8-6). (Note: Other forms of isolation, such as
optical or pneumatic decouplers, which accomplish the same purpose, may be
used and special performance specifications for filters on conductors with
operating signals in the 14 kilohertz to 1-10 gigahertz band may be
established, subject to the approval of the using agency.)
e. Installation within the shielded volume.
(1) Precluding unintentional coupling. It is virtually certain that
the volume enclosed by the TEMPEST shield will contain some BLACK equipment
and wiring, as well as RED circuits that handle national security information.
Therefore, the facility design and hardware/wiring layouts must preclude
unintentional coupling of RED emanations into BLACK conductors. These
measures are above and beyond the shielding and penetration protection
subsystem features and are necessary whether or not a shield is provided.
(2) Sources of additional information. The guidelines and requirements
for RED/BLACK isolation are published in NACSIM 5203 (ref 8-7) and MIL-HDBK-
232A (ref 8-8). Since some details of the specified practices are classified,
this discussion must be considered incomplete, and the designer must also
consult NACSIM 5203 and MIL-HDBK-232A to comply with the minimum requirements.
(3) Limited exclusion area. The room or area within which RED
equipment is located and to which controls are applied for protection of
national security information is known as a limited exclusion area (LEA). The
TEMPEST shield may enclose part or all of the LEA and might also envelope
other sPaces.
(4) Spacing of equipment. RED equipment must be physically separated
from the facility walls and ceiling, from BLACK equipment and wiring, and from
utility conductors such as ventilation ducts and piping. Minimum required
spacings depend on whether the RED equipment is low-level signaling, TEMPEST-
approved hardware or not, and on the nature of possible propagation paths
between the BLACK element and an area of uncontrolled access.
(5) Penetrations. Physical separation practices, as well as special
shielding and distribution (for example, using conduits, ducts, and trays)
instructions, also apply between RED and BLACK wiring in the LEA. Specific
guidelines are presented in NACSIM 5203 for signal lines,
telephone/communication cables, power feeders, ground wires and other utility
(air-conditioning control and status, fire alarm) electrical conductors.
Markings with paint or tape are prescribed to distinguish RED wiring runs from
BLACK cables, and RED conduits must be accessible for inspection.
(6) Separating RED and BLACK. Also, depending on characteristics of
the RED equipment, separate filter-isolated RED and BLACK power distribution
subsystems or individual equipment power filters may be required. Further, it
may be necessary to provide separate and distinctively identified RED and
BLACK convenience outlets.
(7) Telephones and intercoms. Administrative telephone and facility
intercommunication subsystems require particular attention. The most
effective protection is to eliminate or, at least, minimize the number of
instruments in the LEA. If exclusion is not practical, separation, shielding,
and filter isolation devices and positive disconnect capabilities are to be
provided as prescribed in NACSIM 5203.
f. Related TEMPEST documents.
(1) National Security Agency documents. The reader desiring additional
background material concerning TEMPEST and needing specific implementation
information is directed to the series of TEMPEST source documents published by
the National Security Agency (NSA). Supplementary use of these references
during facility design and construction phases is imperative because
classification considerations limit the information incorporated in this
manual to generalized discussions. Only the shielding and penetration
protection requirements are included in this manual.
(2) National COMSEC Information Memorandums. NACSIM 5000 provides an
overall introduction to the TEMPEST discipline (ref 8-9). NACSIM 5203 and
NACSEM 5204 are essential to the project for defining installation
requirements within the protected volume and the shielded enclosure
requirements, respectively (refs 8-7 and 8-4). Other documents to which the
reader may wish to refer include: NACSI 5004 (ref 8-1), NACSI 5005 (ref 8-
10), NACSIM 5100A (ref 8-3), NACSEM 5109 (ref 8-11), NACSEM 5110 (ref 8-12),
and NACSEM 5201 (ref 8-13). The military departments (MILDEPs) also publish
TEMPEST regulations and guidance; access to these documents can be obtained
through the appropriate MILDEP communication security agency.
8-6. Cited references.
8-1. National Telecommunications and Information System Security
Instruction (NTISSI) 7000, 17 October 1988.
8-2. Army Regulation (AR) 530-4, (U) Control of Compromising Emanations
(Headquarters, Department of the Army [HQDA]) (C).
8-3. National COMSEC Information Memorandum (NACSIM) 5100A, (U)
Compromising Emanations Laboratory Test Requirements,
Electromagnetics (NSA) (C).
8-4. National COMSEC/Emergency Security (EMSEC) Information Memorandum
(NACSEM) 5204, (U) Shielded Enclosures (NSA, January 1979) (C).
8-5. Defense Intelligence Agency Memorandum (DIAM) 50-3A, Physical
Security Standards for Sensitive Compartmented Information
Facilities (Defense Intelligence Agency, 2 October 1984).
8-6. Military Standard (MIL-STD) 220A, Method of Insertion-Loss
Measurement (Department of Defense [DOD], 15 December 1959).
8-7. NACSIM 5203, (U) Guidelines for Facility Design and RED/BLACK
Installation (NSA, 30 June 1982) (C).
8-8. Military Handbook (MIL-HDBK) 232A, (U) RED/BLACK Engineering
Guidelines (DOD, 25 April 1980) (C).
8-9. NACSIM 5000, (U) TEMPEST Fundamentals (NSA, 1 February 1982) (C).
8-10. National COMSEC Instruction (NACSI) 5005, (U) TEMPEST
Countermeasures for Facilities Outside the United States (NSA,
January 1984) (S).
8-11. NACSEM 5109, (U) TEMPEST Testing Fundamentals (NSA) (C).
8-12. NACSEM 5110, (U) Facility Evaluation Criteria--TEMPEST (NSA, July
1973) (S).
8-13. NACSEM 5201, (U) TEMPEST Guidelines for Equipment/System Design
(NSA, September 1978) (C).
8-14. DNA EMP Course Study Guide, draft prepared for Defense Nuclear
Agency (The BDM Corporation, April 1983).
Table 8-1. Comparison of HEMP with lightning-induced stresses
on long overhead power lines.
_________________________________________________________________________________
HEMP Vmax Imax dV/dt dI/dt S/Idt2 S/I dt S/IVdt
phenomenon (MV) (kA) (kV/ns) (A/ns) (Coulombs) (A2-sec) (Joules)
_________________________________________________________________________________
HEMP on long 6 14 40 100 10-2 150 6x104
overhead power
lines
_________________________________________________________________________________
HEMP on short 1 2.5 40 100 2x10-3 5 2x103
overhead power
lines
_________________________________________________________________________________
HEMP on buried 1 2.5 8 20 -- -- --
power lines
_________________________________________________________________________________
Direct lightning
strokes (Max) 100 100 0.8 to 8 2 to 100 40 3.1xl06 1.2x108
(Typical) 10 25
_________________________________________________________________________________
Indirect light-
ning strokes
(Max) 6 15 -- -- 4.5 1.8x104 7x106
_________________________________________________________________________________
Voltage computations assume a nominal power line surge impedance of 400 ohms.
Lightning discharge estimates do not consider so-called "positive superbolts"
which are anomalies, but are roughly l0 times more severe than normal
lightning bolts.
_________________________________________________________________________________
[End Chapter 8]
 (4) Compton electrons. At the altitude of the source region, the
Compton electrons travel about 100 meters before they are absorbed. While
traveling this distance, the electrons are strongly deflected by the Earth's
geomagnetic field, making them turn with a radius of about 100 meters. Thus,
the Compton current has large components in nonradial directions from the
burst, i.e., transverse to the direction of the gamma-ray propagation, which
are effective in generating radiated fields. The transverse Compton current
is the primary source of high-altitude radiated EMP. HEMP consists of
radiated electric and magnetic fields that begin almost at once and persist
for more than 100 seconds. Typically, for design-related considerations, only
the fields produced in the first microsecond (early time) after the burst are
considered. However, as the impacts of intermediate and late-time effects
become better defined, additional consideration may be required.
(5) Relationships. In general, characteristics such as the spatial
extent, time waveform, and peak amplitude of HEMP depend on the HOB, weapon
yield, and observer's location with respect to the burst. The following
paragraphs show the characteristics of a nonclassified but representative
HEMP.
b. Electric field. The time waveform of a HEMP electric field, E(t), in
free space can be approximated by the analytic
expression--
kEpkea(t-ts)
E(t) = --------------(kV/m)
l+e(a+b)(t-ts)
(eq 8-1)
where the coefficients are given by--
Epk = 50 kVtm, the peak electric field (kV/meter)
k = 1.2, a normalization constant
a = 5 x 108 sec-1, the exponential rise rate (sec-1)
b = 2.3 x 107 sec-1, the exponential decay rate (sec-1)
Ts = 10-8 sec, the time shift parameter (sec)
t = the time of interest (sec).
Figure 8-2 is a graphic representation of the HEMP waveform.
(4) Compton electrons. At the altitude of the source region, the
Compton electrons travel about 100 meters before they are absorbed. While
traveling this distance, the electrons are strongly deflected by the Earth's
geomagnetic field, making them turn with a radius of about 100 meters. Thus,
the Compton current has large components in nonradial directions from the
burst, i.e., transverse to the direction of the gamma-ray propagation, which
are effective in generating radiated fields. The transverse Compton current
is the primary source of high-altitude radiated EMP. HEMP consists of
radiated electric and magnetic fields that begin almost at once and persist
for more than 100 seconds. Typically, for design-related considerations, only
the fields produced in the first microsecond (early time) after the burst are
considered. However, as the impacts of intermediate and late-time effects
become better defined, additional consideration may be required.
(5) Relationships. In general, characteristics such as the spatial
extent, time waveform, and peak amplitude of HEMP depend on the HOB, weapon
yield, and observer's location with respect to the burst. The following
paragraphs show the characteristics of a nonclassified but representative
HEMP.
b. Electric field. The time waveform of a HEMP electric field, E(t), in
free space can be approximated by the analytic
expression--
kEpkea(t-ts)
E(t) = --------------(kV/m)
l+e(a+b)(t-ts)
(eq 8-1)
where the coefficients are given by--
Epk = 50 kVtm, the peak electric field (kV/meter)
k = 1.2, a normalization constant
a = 5 x 108 sec-1, the exponential rise rate (sec-1)
b = 2.3 x 107 sec-1, the exponential decay rate (sec-1)
Ts = 10-8 sec, the time shift parameter (sec)
t = the time of interest (sec).
Figure 8-2 is a graphic representation of the HEMP waveform.
 c. Magnetic field. The associated magnetic component of the radiated HEMP
field can be obtained by dividing the electric field in volts per meter by 377
ohms. This gives the magnetic field in amps per meter with a peak value of
about 135 amps per meter. It should be noted, however, that the values shown
in figure 8-2 apply only to the free-field environment and not to the behavior
of fields near conducting surfaces such as the surface of the Earth. Near
such a conductor, the electric field will be much smaller because it is
shorted out, whereas the magnetic field will be about twice its value in free
space, or almost 270 amps per meter.
d. Spatial extent.
(1) Geographical coverage. The geographical coverage of HEMP over the
Earth's surface is determined entirely by the HOB. The maximum ground range
(tangent radius) depends on the tangent to the Earth from the burst point and
is the arc length between this tangent and the point on the Earth's surface
directly beneath the burst surface zero. To approximate this distance, the
following calculation for tangent radius RT (in kilometers) can be made:
RE
RT = RE cos-1(----------)
RE + HOB
(eq 8-2)
where RE = 6370 kilometers (the approximate radius of the Earth) and HOB is
the burst height in kilometers.
(2) Surface area calculation. The total surface area AT in square
kilometers covered by HEMP can be calculated as follows:
2(pi)RE2 HOB
AT = ------------
RE + HOB
(eq 8-3)
Figure 8-3 applies this information to the United States, showing ground
coverage for bursts of 50 and 120 miles over the central portion.
c. Magnetic field. The associated magnetic component of the radiated HEMP
field can be obtained by dividing the electric field in volts per meter by 377
ohms. This gives the magnetic field in amps per meter with a peak value of
about 135 amps per meter. It should be noted, however, that the values shown
in figure 8-2 apply only to the free-field environment and not to the behavior
of fields near conducting surfaces such as the surface of the Earth. Near
such a conductor, the electric field will be much smaller because it is
shorted out, whereas the magnetic field will be about twice its value in free
space, or almost 270 amps per meter.
d. Spatial extent.
(1) Geographical coverage. The geographical coverage of HEMP over the
Earth's surface is determined entirely by the HOB. The maximum ground range
(tangent radius) depends on the tangent to the Earth from the burst point and
is the arc length between this tangent and the point on the Earth's surface
directly beneath the burst surface zero. To approximate this distance, the
following calculation for tangent radius RT (in kilometers) can be made:
RE
RT = RE cos-1(----------)
RE + HOB
(eq 8-2)
where RE = 6370 kilometers (the approximate radius of the Earth) and HOB is
the burst height in kilometers.
(2) Surface area calculation. The total surface area AT in square
kilometers covered by HEMP can be calculated as follows:
2(pi)RE2 HOB
AT = ------------
RE + HOB
(eq 8-3)
Figure 8-3 applies this information to the United States, showing ground
coverage for bursts of 50 and 120 miles over the central portion.
 e. HEMP peak fields at the Earth's surface.
(1) Orientation of Earth's geomagnetic field. Since the motion of the
compton electrons depends on the orientation of the Earth's geomagnetic field,
the incident HEMP fields vary significantly in peak amplitude, rise time, and
duration over the large area affected by the HEMP. The maximum peak electric
field Emax occurs just south of ground zero and can be as high as 50 kilovolts
per meter, depending on the HOB and the weapon yield. The peak field Epk
observed at any other location is some fraction of Emax.
(2) Geometric factors. In addition to the orientation and dip of the
geomagnetic field, geometric factors based on the observer's position with
respect to the burst also cause spatial variations of the HEMP field strength.
In the figure, the null area slightly north of the burst point is produced by
the geomagnetic dip over the CONUS; Compton electrons created in the same
direction as the Earth's geomagnetic field do not turn and no radiated fields
are created. The maximum peak fields are found at a distance equal to about
twice the HOB south of surface zero.
8-4. Comparison of HEMP and lightning. HEMP-induced surge currents on
overhead transmission lines are similar to, but not exactly the same as,
lightning-induced surges. Table 8-1 compares worst-case surges. From the
numerical values, it could be inferred that lightning is a more serious
threat. The values for lightning, however, represent the 99th percentile of
all measurements on standard lightning discharges, and thus may not be
representative of the strokes that occur near a given facility. In contrast,
the HEMP pulse is not a localized phenomenon, but illuminates a very wide
area. As a result, any hardened facility would see a HEMP-induced current if
there were a war, while it might never be exposed to the maximum lightning
current. In addition, there are significant differences in pulse rate and
frequency content. For this reason, it cannot be assumed that standard
lightning protection is an adequate substitute for HEMP protection.
8-5. TEMPEST risks.
a. TEMPEST objectives.
(1) Communication security (COMSEC). Communication security (COMSEC)
is the term used to denote steps taken to prevent disclosure of national
security information to unauthorized recipients during the communication
process. NTISSI 7000 and AR 530-4 define minimum measures that must be taken
to protect CONUS facilities (refs 8-1 and 8-2). The information to be guarded
includes plain text of classified messages, as well as cryptographic
technology and materials. Cryptographic information is especially sensitive,
not as an end in itself, but because it is used to protect other classified
data. If the integrity of an encryption system is breached at any point, all
classified information protected by that coding may be compromised.
(2) Parts of COMSEC. COMSEC consists of four main parts: physical
security--all physical measures to safeguard materials from unauthorized
access; emissions security-control of emanations from equipments processing
classified data; transmission security--protection of transmissions from
traffic analysis, imitative deception, and disruption; and cryptographic
security--the use of technically sound cryptosystems. Only the emissions
security discipline or TEMPEST is specifically addressed in this manual.
(3) Details of TEMPEST issues. Because the details of many TEMPEST
issues are classified and controlled under strict conditions of need-to-know,
the following discussions must be somewhat general. Nevertheless, it provides
the reader with a needed aPpreciation of TEMPEST fundamentals.
(4) Theory of electromagnetic signal emanation. Any
electrical/electronic circuit that carries a time-varying current will emanate
electromagnetic signals with the strength of the emission proportional to the
current amplitude and its time rate of change. These signals propagate
outward from the source as free space waves and as guided waves along
conductors connected to or close to the radiator. If time variations of the
source currents are related in any way to the information content of the
signals (which will almost certainly be the case on a data line~, then the
emanation will also bear some relationship to the data. It may, therefore, be
possible to reconstruct the original intelligence by analysis of these
unintentional emissions.
(5) Aim of TEMPEST discipline. Finally, if the source information is
classified, interception and analysis of the emanations by unauthorized
personnel will compromise national security. The aim of the TEMPEST
discipline is to control stray emissions in a manner that prevents such
disclosures.
b. Equipment emission characteristics.
(1) RED and BLACK terminology. Before addressing the emission
characteristics issue, the RED and BLACK terminology will first be introduced.
A RED equipment or circuit is one that handles plain text information with
national security value. Equipment processing signals that are unclassified,
either because of content of the text or because the intelligence is obscured
by encryption, is denoted in BLACK.
(2) Strength and nature of emanations. The unintentional emission
characteristics of RED systems and equipments are categorized according to
strength and nature of their emanations. The reason for the strength element
is clear: high-level signals can be intercepted at magnitudes that permit
analysis with greater physical separations between the source and the
eavesdropper. The second factor relates to the correlation between waveform
of the emitted signal and the information to be protected.
(3) Classes of equipment. For purposes of facility engineering and
construction within the limitations of this manual, it is only necessary to
define two classes:
(a) Equipments that are TEMPEST-approved according to the criteria
established in the current edition of NACSIM 5100 (ref 8-3).
(b) All equipments that have not been TEMPEST-tested or are
nonapproved.
(4) Project development brochure. Information regarding the category
of RED equipment to be protected should be presented in the project
development brochure prepared by the user of the facility.
c. Detection capabilities.
(1) Electromagnetic surveillance concerns. Concerns about
electromagnetic surveillance have been intensified by advances in state-of-
the-art equipment design and signal processing techniques. While a few
technologies such as fiber optics and multiplexing have made interception and
analysis more difficult, the overall effect has been to open new opportunities
for eavesdroppers. Projections into the immediate future indicate that this
trend will continue.
(2) Worst-case evaluation. The only safe approach is a reasonable
worst-case evaluation. It must be assumed that the opposition has the proper
equipment to monitor all signals of significant amplitude in areas where
access is uncontrolled.
d. TEMPEST isolation requirements.
(1) Isolation approaches. Encryption is the method used to guard
against disclosure of classified information when long-distance
telecommunications are monitored. However, it does not prevent possible
compromise through interceptions and analyses of unintentional emanations from
RED equipments.
(a) Many approaches are available to equipment and facility
designers to avoid disclosures through potentially compromising emanations.
All of these techniques reduce the stray signal strength at locations where
access is uncontrolled, so that the intelligence content is lost in the
background electrical noise. AR 530-4 should be consulted to determine the
level of protection required.
(b) Examples of preventive measures include the following:
- Physical separation--excluding unauthorized individuals from
areas near the source where the emanations are larger in amplitude than the
ambient noise.
- Electromagnetic separation--the use of shielding, filtering,
and other methods of EM isolation to attenuate the unintentional emissions.
- Signal level minimization--design and operation of circuits at
lowest feasible power levels to minimize the strength of unintentional
emissions.
(c) These methods can be employed in an infinite variety of
combinations to achieve the desired goals.
(2) Recommended TEMPEST isolation concept. NTISSI 7000 and AR 530-4
analysis is the first step in determining needed TEMPEST countermeasures.
Shielding for TEMPEST is not necessarily required; however, for facilities
having high-confidence HEMP survivability specifications and being hardened in
accordance with recommendations of this manual, it is technically prudent and
highly cost-effective to include TEMPEST shielding and penetration protection
in a common subsystem. The suggested TEMPEST isolation concept takes
advantage of this principle.
(a) The first requirement, a physical security measure, is the
establishment of a controlled space (CS) containing the equipment to be
TEMPEST-protected and within which access is not available to those not
authorized to receive the information being processed at the site.
(b) NACSEM 5204 defines the detailed procedures to compute shielding
effectiveness requirements for specific TEMPEST applications (ref 8-4).
Parameters of the problem include measured emission characteristics of the
equipments and distance to the perimeter of the controlled space. The
calculation determines the attenuation needed to reduce emanation levels below
detectable limits in the ambient noise environment. If reasonable worst-case
assumptions are made regarding the variables, however, then 50 decibels
(nominal) attenuation is adequate for an installation within CONUS. This
requirement can be met by a shield and penetration treatments that conform to
Specification NSA No. 73-2A.
(c) NSA 73-2A is an appendix in NACSEM 5204. The document also
contains Specifications NSA No. 65-5 and 65-6 for TEMPEST applications where
greater shielding effectiveness requirements exist. DIAM 50-3A should be
consulted for SCIF shielding information (ref 8-5).
(3) TEMPEST design criteria. Since electromagnetic performance
requirements of a 50-decibel (nominal) TEMPEST design are quite consistent
with performance necessary for HEMP considerations and only a few additional
features are prescribed for the shielding and penetration protection
subsystem, the reasonable worst-case TEMPEST assumptions have been
incorporated into the recommended HEMP/TEMPEST approach. The following
paragraphs summarize the TEMPEST-unique requirements for facility design.
(a) Shielding effectiveness. Minimum attenuation levels of the
shielded enclosure, when measured in accordance with NSA 73-2A, are as shown
in figure 8-4. This curve contains a slight increase in the requirements at
frequencies above 500 megahertz compared with values prescribed in NSA 73-2A.
The upper frequency of the shielding effectiveness and filter insertion loss
frequency have also been extended as high as 10 gigahertz. The site-specific
requirements should be determined by consulting with the using agency.
e. HEMP peak fields at the Earth's surface.
(1) Orientation of Earth's geomagnetic field. Since the motion of the
compton electrons depends on the orientation of the Earth's geomagnetic field,
the incident HEMP fields vary significantly in peak amplitude, rise time, and
duration over the large area affected by the HEMP. The maximum peak electric
field Emax occurs just south of ground zero and can be as high as 50 kilovolts
per meter, depending on the HOB and the weapon yield. The peak field Epk
observed at any other location is some fraction of Emax.
(2) Geometric factors. In addition to the orientation and dip of the
geomagnetic field, geometric factors based on the observer's position with
respect to the burst also cause spatial variations of the HEMP field strength.
In the figure, the null area slightly north of the burst point is produced by
the geomagnetic dip over the CONUS; Compton electrons created in the same
direction as the Earth's geomagnetic field do not turn and no radiated fields
are created. The maximum peak fields are found at a distance equal to about
twice the HOB south of surface zero.
8-4. Comparison of HEMP and lightning. HEMP-induced surge currents on
overhead transmission lines are similar to, but not exactly the same as,
lightning-induced surges. Table 8-1 compares worst-case surges. From the
numerical values, it could be inferred that lightning is a more serious
threat. The values for lightning, however, represent the 99th percentile of
all measurements on standard lightning discharges, and thus may not be
representative of the strokes that occur near a given facility. In contrast,
the HEMP pulse is not a localized phenomenon, but illuminates a very wide
area. As a result, any hardened facility would see a HEMP-induced current if
there were a war, while it might never be exposed to the maximum lightning
current. In addition, there are significant differences in pulse rate and
frequency content. For this reason, it cannot be assumed that standard
lightning protection is an adequate substitute for HEMP protection.
8-5. TEMPEST risks.
a. TEMPEST objectives.
(1) Communication security (COMSEC). Communication security (COMSEC)
is the term used to denote steps taken to prevent disclosure of national
security information to unauthorized recipients during the communication
process. NTISSI 7000 and AR 530-4 define minimum measures that must be taken
to protect CONUS facilities (refs 8-1 and 8-2). The information to be guarded
includes plain text of classified messages, as well as cryptographic
technology and materials. Cryptographic information is especially sensitive,
not as an end in itself, but because it is used to protect other classified
data. If the integrity of an encryption system is breached at any point, all
classified information protected by that coding may be compromised.
(2) Parts of COMSEC. COMSEC consists of four main parts: physical
security--all physical measures to safeguard materials from unauthorized
access; emissions security-control of emanations from equipments processing
classified data; transmission security--protection of transmissions from
traffic analysis, imitative deception, and disruption; and cryptographic
security--the use of technically sound cryptosystems. Only the emissions
security discipline or TEMPEST is specifically addressed in this manual.
(3) Details of TEMPEST issues. Because the details of many TEMPEST
issues are classified and controlled under strict conditions of need-to-know,
the following discussions must be somewhat general. Nevertheless, it provides
the reader with a needed aPpreciation of TEMPEST fundamentals.
(4) Theory of electromagnetic signal emanation. Any
electrical/electronic circuit that carries a time-varying current will emanate
electromagnetic signals with the strength of the emission proportional to the
current amplitude and its time rate of change. These signals propagate
outward from the source as free space waves and as guided waves along
conductors connected to or close to the radiator. If time variations of the
source currents are related in any way to the information content of the
signals (which will almost certainly be the case on a data line~, then the
emanation will also bear some relationship to the data. It may, therefore, be
possible to reconstruct the original intelligence by analysis of these
unintentional emissions.
(5) Aim of TEMPEST discipline. Finally, if the source information is
classified, interception and analysis of the emanations by unauthorized
personnel will compromise national security. The aim of the TEMPEST
discipline is to control stray emissions in a manner that prevents such
disclosures.
b. Equipment emission characteristics.
(1) RED and BLACK terminology. Before addressing the emission
characteristics issue, the RED and BLACK terminology will first be introduced.
A RED equipment or circuit is one that handles plain text information with
national security value. Equipment processing signals that are unclassified,
either because of content of the text or because the intelligence is obscured
by encryption, is denoted in BLACK.
(2) Strength and nature of emanations. The unintentional emission
characteristics of RED systems and equipments are categorized according to
strength and nature of their emanations. The reason for the strength element
is clear: high-level signals can be intercepted at magnitudes that permit
analysis with greater physical separations between the source and the
eavesdropper. The second factor relates to the correlation between waveform
of the emitted signal and the information to be protected.
(3) Classes of equipment. For purposes of facility engineering and
construction within the limitations of this manual, it is only necessary to
define two classes:
(a) Equipments that are TEMPEST-approved according to the criteria
established in the current edition of NACSIM 5100 (ref 8-3).
(b) All equipments that have not been TEMPEST-tested or are
nonapproved.
(4) Project development brochure. Information regarding the category
of RED equipment to be protected should be presented in the project
development brochure prepared by the user of the facility.
c. Detection capabilities.
(1) Electromagnetic surveillance concerns. Concerns about
electromagnetic surveillance have been intensified by advances in state-of-
the-art equipment design and signal processing techniques. While a few
technologies such as fiber optics and multiplexing have made interception and
analysis more difficult, the overall effect has been to open new opportunities
for eavesdroppers. Projections into the immediate future indicate that this
trend will continue.
(2) Worst-case evaluation. The only safe approach is a reasonable
worst-case evaluation. It must be assumed that the opposition has the proper
equipment to monitor all signals of significant amplitude in areas where
access is uncontrolled.
d. TEMPEST isolation requirements.
(1) Isolation approaches. Encryption is the method used to guard
against disclosure of classified information when long-distance
telecommunications are monitored. However, it does not prevent possible
compromise through interceptions and analyses of unintentional emanations from
RED equipments.
(a) Many approaches are available to equipment and facility
designers to avoid disclosures through potentially compromising emanations.
All of these techniques reduce the stray signal strength at locations where
access is uncontrolled, so that the intelligence content is lost in the
background electrical noise. AR 530-4 should be consulted to determine the
level of protection required.
(b) Examples of preventive measures include the following:
- Physical separation--excluding unauthorized individuals from
areas near the source where the emanations are larger in amplitude than the
ambient noise.
- Electromagnetic separation--the use of shielding, filtering,
and other methods of EM isolation to attenuate the unintentional emissions.
- Signal level minimization--design and operation of circuits at
lowest feasible power levels to minimize the strength of unintentional
emissions.
(c) These methods can be employed in an infinite variety of
combinations to achieve the desired goals.
(2) Recommended TEMPEST isolation concept. NTISSI 7000 and AR 530-4
analysis is the first step in determining needed TEMPEST countermeasures.
Shielding for TEMPEST is not necessarily required; however, for facilities
having high-confidence HEMP survivability specifications and being hardened in
accordance with recommendations of this manual, it is technically prudent and
highly cost-effective to include TEMPEST shielding and penetration protection
in a common subsystem. The suggested TEMPEST isolation concept takes
advantage of this principle.
(a) The first requirement, a physical security measure, is the
establishment of a controlled space (CS) containing the equipment to be
TEMPEST-protected and within which access is not available to those not
authorized to receive the information being processed at the site.
(b) NACSEM 5204 defines the detailed procedures to compute shielding
effectiveness requirements for specific TEMPEST applications (ref 8-4).
Parameters of the problem include measured emission characteristics of the
equipments and distance to the perimeter of the controlled space. The
calculation determines the attenuation needed to reduce emanation levels below
detectable limits in the ambient noise environment. If reasonable worst-case
assumptions are made regarding the variables, however, then 50 decibels
(nominal) attenuation is adequate for an installation within CONUS. This
requirement can be met by a shield and penetration treatments that conform to
Specification NSA No. 73-2A.
(c) NSA 73-2A is an appendix in NACSEM 5204. The document also
contains Specifications NSA No. 65-5 and 65-6 for TEMPEST applications where
greater shielding effectiveness requirements exist. DIAM 50-3A should be
consulted for SCIF shielding information (ref 8-5).
(3) TEMPEST design criteria. Since electromagnetic performance
requirements of a 50-decibel (nominal) TEMPEST design are quite consistent
with performance necessary for HEMP considerations and only a few additional
features are prescribed for the shielding and penetration protection
subsystem, the reasonable worst-case TEMPEST assumptions have been
incorporated into the recommended HEMP/TEMPEST approach. The following
paragraphs summarize the TEMPEST-unique requirements for facility design.
(a) Shielding effectiveness. Minimum attenuation levels of the
shielded enclosure, when measured in accordance with NSA 73-2A, are as shown
in figure 8-4. This curve contains a slight increase in the requirements at
frequencies above 500 megahertz compared with values prescribed in NSA 73-2A.
The upper frequency of the shielding effectiveness and filter insertion loss
frequency have also been extended as high as 10 gigahertz. The site-specific
requirements should be determined by consulting with the using agency.
 (b) Shield doors. TEMPEST shield design includes a shielded
vestibule entrance arrangement with two doors oriented at 90 degrees to each
other. The purpose of double doors is the same as that cited for HEMP--to
preserve the shielding effectiveness during actual entries and exits.
Effectiveness requirements for the doors are the same as those for the main
shield.
(c) Piping and ventilation penetration. Mechanical penetrations,
piping, and air ducts are to be bonded to the shield at the point of
penetration. The design must be configured as a waveguide-beyond-cutoff to
attenuate all frequencies within the specified band, as shown in figure 8-5.
(b) Shield doors. TEMPEST shield design includes a shielded
vestibule entrance arrangement with two doors oriented at 90 degrees to each
other. The purpose of double doors is the same as that cited for HEMP--to
preserve the shielding effectiveness during actual entries and exits.
Effectiveness requirements for the doors are the same as those for the main
shield.
(c) Piping and ventilation penetration. Mechanical penetrations,
piping, and air ducts are to be bonded to the shield at the point of
penetration. The design must be configured as a waveguide-beyond-cutoff to
attenuate all frequencies within the specified band, as shown in figure 8-5.
 (d) Electrical penetration. The specification requires that a
filter providing at least 50 decibels of insertion loss from 14 kilohertz to
the upper design protection frequency, typically 1 to 10-gigahertz upper
frequency when measured in accordance with procedures of MIL-STD-220A, be
installed on each power, telephone, and signal line that penetrates the
enclosure shield wall (ref 8-6). (Note: Other forms of isolation, such as
optical or pneumatic decouplers, which accomplish the same purpose, may be
used and special performance specifications for filters on conductors with
operating signals in the 14 kilohertz to 1-10 gigahertz band may be
established, subject to the approval of the using agency.)
e. Installation within the shielded volume.
(1) Precluding unintentional coupling. It is virtually certain that
the volume enclosed by the TEMPEST shield will contain some BLACK equipment
and wiring, as well as RED circuits that handle national security information.
Therefore, the facility design and hardware/wiring layouts must preclude
unintentional coupling of RED emanations into BLACK conductors. These
measures are above and beyond the shielding and penetration protection
subsystem features and are necessary whether or not a shield is provided.
(2) Sources of additional information. The guidelines and requirements
for RED/BLACK isolation are published in NACSIM 5203 (ref 8-7) and MIL-HDBK-
232A (ref 8-8). Since some details of the specified practices are classified,
this discussion must be considered incomplete, and the designer must also
consult NACSIM 5203 and MIL-HDBK-232A to comply with the minimum requirements.
(3) Limited exclusion area. The room or area within which RED
equipment is located and to which controls are applied for protection of
national security information is known as a limited exclusion area (LEA). The
TEMPEST shield may enclose part or all of the LEA and might also envelope
other sPaces.
(4) Spacing of equipment. RED equipment must be physically separated
from the facility walls and ceiling, from BLACK equipment and wiring, and from
utility conductors such as ventilation ducts and piping. Minimum required
spacings depend on whether the RED equipment is low-level signaling, TEMPEST-
approved hardware or not, and on the nature of possible propagation paths
between the BLACK element and an area of uncontrolled access.
(5) Penetrations. Physical separation practices, as well as special
shielding and distribution (for example, using conduits, ducts, and trays)
instructions, also apply between RED and BLACK wiring in the LEA. Specific
guidelines are presented in NACSIM 5203 for signal lines,
telephone/communication cables, power feeders, ground wires and other utility
(air-conditioning control and status, fire alarm) electrical conductors.
Markings with paint or tape are prescribed to distinguish RED wiring runs from
BLACK cables, and RED conduits must be accessible for inspection.
(6) Separating RED and BLACK. Also, depending on characteristics of
the RED equipment, separate filter-isolated RED and BLACK power distribution
subsystems or individual equipment power filters may be required. Further, it
may be necessary to provide separate and distinctively identified RED and
BLACK convenience outlets.
(7) Telephones and intercoms. Administrative telephone and facility
intercommunication subsystems require particular attention. The most
effective protection is to eliminate or, at least, minimize the number of
instruments in the LEA. If exclusion is not practical, separation, shielding,
and filter isolation devices and positive disconnect capabilities are to be
provided as prescribed in NACSIM 5203.
f. Related TEMPEST documents.
(1) National Security Agency documents. The reader desiring additional
background material concerning TEMPEST and needing specific implementation
information is directed to the series of TEMPEST source documents published by
the National Security Agency (NSA). Supplementary use of these references
during facility design and construction phases is imperative because
classification considerations limit the information incorporated in this
manual to generalized discussions. Only the shielding and penetration
protection requirements are included in this manual.
(2) National COMSEC Information Memorandums. NACSIM 5000 provides an
overall introduction to the TEMPEST discipline (ref 8-9). NACSIM 5203 and
NACSEM 5204 are essential to the project for defining installation
requirements within the protected volume and the shielded enclosure
requirements, respectively (refs 8-7 and 8-4). Other documents to which the
reader may wish to refer include: NACSI 5004 (ref 8-1), NACSI 5005 (ref 8-
10), NACSIM 5100A (ref 8-3), NACSEM 5109 (ref 8-11), NACSEM 5110 (ref 8-12),
and NACSEM 5201 (ref 8-13). The military departments (MILDEPs) also publish
TEMPEST regulations and guidance; access to these documents can be obtained
through the appropriate MILDEP communication security agency.
8-6. Cited references.
8-1. National Telecommunications and Information System Security
Instruction (NTISSI) 7000, 17 October 1988.
8-2. Army Regulation (AR) 530-4, (U) Control of Compromising Emanations
(Headquarters, Department of the Army [HQDA]) (C).
8-3. National COMSEC Information Memorandum (NACSIM) 5100A, (U)
Compromising Emanations Laboratory Test Requirements,
Electromagnetics (NSA) (C).
8-4. National COMSEC/Emergency Security (EMSEC) Information Memorandum
(NACSEM) 5204, (U) Shielded Enclosures (NSA, January 1979) (C).
8-5. Defense Intelligence Agency Memorandum (DIAM) 50-3A, Physical
Security Standards for Sensitive Compartmented Information
Facilities (Defense Intelligence Agency, 2 October 1984).
8-6. Military Standard (MIL-STD) 220A, Method of Insertion-Loss
Measurement (Department of Defense [DOD], 15 December 1959).
8-7. NACSIM 5203, (U) Guidelines for Facility Design and RED/BLACK
Installation (NSA, 30 June 1982) (C).
8-8. Military Handbook (MIL-HDBK) 232A, (U) RED/BLACK Engineering
Guidelines (DOD, 25 April 1980) (C).
8-9. NACSIM 5000, (U) TEMPEST Fundamentals (NSA, 1 February 1982) (C).
8-10. National COMSEC Instruction (NACSI) 5005, (U) TEMPEST
Countermeasures for Facilities Outside the United States (NSA,
January 1984) (S).
8-11. NACSEM 5109, (U) TEMPEST Testing Fundamentals (NSA) (C).
8-12. NACSEM 5110, (U) Facility Evaluation Criteria--TEMPEST (NSA, July
1973) (S).
8-13. NACSEM 5201, (U) TEMPEST Guidelines for Equipment/System Design
(NSA, September 1978) (C).
8-14. DNA EMP Course Study Guide, draft prepared for Defense Nuclear
Agency (The BDM Corporation, April 1983).
Table 8-1. Comparison of HEMP with lightning-induced stresses
on long overhead power lines.
_________________________________________________________________________________
HEMP Vmax Imax dV/dt dI/dt S/Idt2 S/I dt S/IVdt
phenomenon (MV) (kA) (kV/ns) (A/ns) (Coulombs) (A2-sec) (Joules)
_________________________________________________________________________________
HEMP on long 6 14 40 100 10-2 150 6x104
overhead power
lines
_________________________________________________________________________________
HEMP on short 1 2.5 40 100 2x10-3 5 2x103
overhead power
lines
_________________________________________________________________________________
HEMP on buried 1 2.5 8 20 -- -- --
power lines
_________________________________________________________________________________
Direct lightning
strokes (Max) 100 100 0.8 to 8 2 to 100 40 3.1xl06 1.2x108
(Typical) 10 25
_________________________________________________________________________________
Indirect light-
ning strokes
(Max) 6 15 -- -- 4.5 1.8x104 7x106
_________________________________________________________________________________
Voltage computations assume a nominal power line surge impedance of 400 ohms.
Lightning discharge estimates do not consider so-called "positive superbolts"
which are anomalies, but are roughly l0 times more severe than normal
lightning bolts.
_________________________________________________________________________________
[End Chapter 8]
(d) Electrical penetration. The specification requires that a
filter providing at least 50 decibels of insertion loss from 14 kilohertz to
the upper design protection frequency, typically 1 to 10-gigahertz upper
frequency when measured in accordance with procedures of MIL-STD-220A, be
installed on each power, telephone, and signal line that penetrates the
enclosure shield wall (ref 8-6). (Note: Other forms of isolation, such as
optical or pneumatic decouplers, which accomplish the same purpose, may be
used and special performance specifications for filters on conductors with
operating signals in the 14 kilohertz to 1-10 gigahertz band may be
established, subject to the approval of the using agency.)
e. Installation within the shielded volume.
(1) Precluding unintentional coupling. It is virtually certain that
the volume enclosed by the TEMPEST shield will contain some BLACK equipment
and wiring, as well as RED circuits that handle national security information.
Therefore, the facility design and hardware/wiring layouts must preclude
unintentional coupling of RED emanations into BLACK conductors. These
measures are above and beyond the shielding and penetration protection
subsystem features and are necessary whether or not a shield is provided.
(2) Sources of additional information. The guidelines and requirements
for RED/BLACK isolation are published in NACSIM 5203 (ref 8-7) and MIL-HDBK-
232A (ref 8-8). Since some details of the specified practices are classified,
this discussion must be considered incomplete, and the designer must also
consult NACSIM 5203 and MIL-HDBK-232A to comply with the minimum requirements.
(3) Limited exclusion area. The room or area within which RED
equipment is located and to which controls are applied for protection of
national security information is known as a limited exclusion area (LEA). The
TEMPEST shield may enclose part or all of the LEA and might also envelope
other sPaces.
(4) Spacing of equipment. RED equipment must be physically separated
from the facility walls and ceiling, from BLACK equipment and wiring, and from
utility conductors such as ventilation ducts and piping. Minimum required
spacings depend on whether the RED equipment is low-level signaling, TEMPEST-
approved hardware or not, and on the nature of possible propagation paths
between the BLACK element and an area of uncontrolled access.
(5) Penetrations. Physical separation practices, as well as special
shielding and distribution (for example, using conduits, ducts, and trays)
instructions, also apply between RED and BLACK wiring in the LEA. Specific
guidelines are presented in NACSIM 5203 for signal lines,
telephone/communication cables, power feeders, ground wires and other utility
(air-conditioning control and status, fire alarm) electrical conductors.
Markings with paint or tape are prescribed to distinguish RED wiring runs from
BLACK cables, and RED conduits must be accessible for inspection.
(6) Separating RED and BLACK. Also, depending on characteristics of
the RED equipment, separate filter-isolated RED and BLACK power distribution
subsystems or individual equipment power filters may be required. Further, it
may be necessary to provide separate and distinctively identified RED and
BLACK convenience outlets.
(7) Telephones and intercoms. Administrative telephone and facility
intercommunication subsystems require particular attention. The most
effective protection is to eliminate or, at least, minimize the number of
instruments in the LEA. If exclusion is not practical, separation, shielding,
and filter isolation devices and positive disconnect capabilities are to be
provided as prescribed in NACSIM 5203.
f. Related TEMPEST documents.
(1) National Security Agency documents. The reader desiring additional
background material concerning TEMPEST and needing specific implementation
information is directed to the series of TEMPEST source documents published by
the National Security Agency (NSA). Supplementary use of these references
during facility design and construction phases is imperative because
classification considerations limit the information incorporated in this
manual to generalized discussions. Only the shielding and penetration
protection requirements are included in this manual.
(2) National COMSEC Information Memorandums. NACSIM 5000 provides an
overall introduction to the TEMPEST discipline (ref 8-9). NACSIM 5203 and
NACSEM 5204 are essential to the project for defining installation
requirements within the protected volume and the shielded enclosure
requirements, respectively (refs 8-7 and 8-4). Other documents to which the
reader may wish to refer include: NACSI 5004 (ref 8-1), NACSI 5005 (ref 8-
10), NACSIM 5100A (ref 8-3), NACSEM 5109 (ref 8-11), NACSEM 5110 (ref 8-12),
and NACSEM 5201 (ref 8-13). The military departments (MILDEPs) also publish
TEMPEST regulations and guidance; access to these documents can be obtained
through the appropriate MILDEP communication security agency.
8-6. Cited references.
8-1. National Telecommunications and Information System Security
Instruction (NTISSI) 7000, 17 October 1988.
8-2. Army Regulation (AR) 530-4, (U) Control of Compromising Emanations
(Headquarters, Department of the Army [HQDA]) (C).
8-3. National COMSEC Information Memorandum (NACSIM) 5100A, (U)
Compromising Emanations Laboratory Test Requirements,
Electromagnetics (NSA) (C).
8-4. National COMSEC/Emergency Security (EMSEC) Information Memorandum
(NACSEM) 5204, (U) Shielded Enclosures (NSA, January 1979) (C).
8-5. Defense Intelligence Agency Memorandum (DIAM) 50-3A, Physical
Security Standards for Sensitive Compartmented Information
Facilities (Defense Intelligence Agency, 2 October 1984).
8-6. Military Standard (MIL-STD) 220A, Method of Insertion-Loss
Measurement (Department of Defense [DOD], 15 December 1959).
8-7. NACSIM 5203, (U) Guidelines for Facility Design and RED/BLACK
Installation (NSA, 30 June 1982) (C).
8-8. Military Handbook (MIL-HDBK) 232A, (U) RED/BLACK Engineering
Guidelines (DOD, 25 April 1980) (C).
8-9. NACSIM 5000, (U) TEMPEST Fundamentals (NSA, 1 February 1982) (C).
8-10. National COMSEC Instruction (NACSI) 5005, (U) TEMPEST
Countermeasures for Facilities Outside the United States (NSA,
January 1984) (S).
8-11. NACSEM 5109, (U) TEMPEST Testing Fundamentals (NSA) (C).
8-12. NACSEM 5110, (U) Facility Evaluation Criteria--TEMPEST (NSA, July
1973) (S).
8-13. NACSEM 5201, (U) TEMPEST Guidelines for Equipment/System Design
(NSA, September 1978) (C).
8-14. DNA EMP Course Study Guide, draft prepared for Defense Nuclear
Agency (The BDM Corporation, April 1983).
Table 8-1. Comparison of HEMP with lightning-induced stresses
on long overhead power lines.
_________________________________________________________________________________
HEMP Vmax Imax dV/dt dI/dt S/Idt2 S/I dt S/IVdt
phenomenon (MV) (kA) (kV/ns) (A/ns) (Coulombs) (A2-sec) (Joules)
_________________________________________________________________________________
HEMP on long 6 14 40 100 10-2 150 6x104
overhead power
lines
_________________________________________________________________________________
HEMP on short 1 2.5 40 100 2x10-3 5 2x103
overhead power
lines
_________________________________________________________________________________
HEMP on buried 1 2.5 8 20 -- -- --
power lines
_________________________________________________________________________________
Direct lightning
strokes (Max) 100 100 0.8 to 8 2 to 100 40 3.1xl06 1.2x108
(Typical) 10 25
_________________________________________________________________________________
Indirect light-
ning strokes
(Max) 6 15 -- -- 4.5 1.8x104 7x106
_________________________________________________________________________________
Voltage computations assume a nominal power line surge impedance of 400 ohms.
Lightning discharge estimates do not consider so-called "positive superbolts"
which are anomalies, but are roughly l0 times more severe than normal
lightning bolts.
_________________________________________________________________________________
[End Chapter 8]